Unconfigured Qt X devices or devices and systems that have not been protected will be at risk from malicious attacks. Such attacks include denial of service, intentional mis-configuration and theft of credentials if deployed on a network that is not firewalled or adequately protected. Qt X devices are shipped in an 'unprotected' state to allow installers to configure and use the device without requiring explicit authentication or authorization. Protected devices and systems will require authentication and authorization enabled by the user either through this software or via the WebUI.
Click here for information on security certificates.
Users may password-protect a system via the Security button on the Devices & Systems window. A system must be selected from the list for the security button ( ) to be available:
To protect a system click the Security button as shown above. The following dialog will appear on an unprotected system:
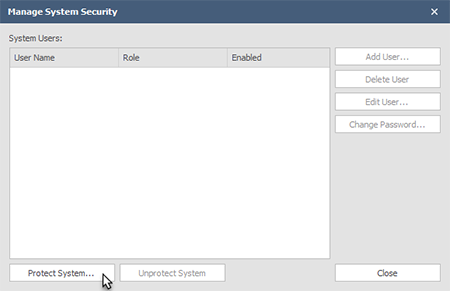
Click Protect System to add security settings. When a system is protected for the first time the user must set up an Admin account. This account will have rights to all settings, including creating and deleting users and setting their level of access:
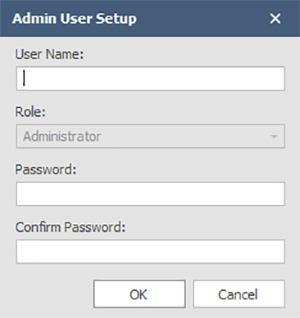
Passwords must be between 8 and 64 characters. Once an administrator account has been created, other user roles may be assigned:
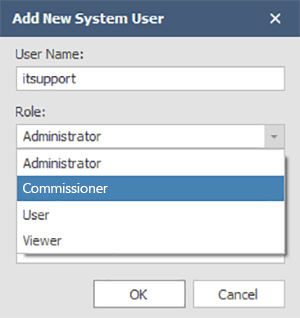
The below table gives a high-level overview of the types of permission each user role has:
|
User Role |
Permissions |
|---|---|
|
Administrator |
Full access - may create users, un-protect/protect a system, etc. |
|
Commissioner |
Same permissions as the Administrator except they may not create new users, make changes to the network protocols or manage security certificates. |
|
User |
Some ability to change settings, such as zones, time/date, scheduling, etc. |
|
Viewer |
Read-only; cannot make any changes to devices or systems. |
For detailed descriptions of user roles, see the tables below.
The System Security window will reflect the System Users and their respective roles once they have been created:
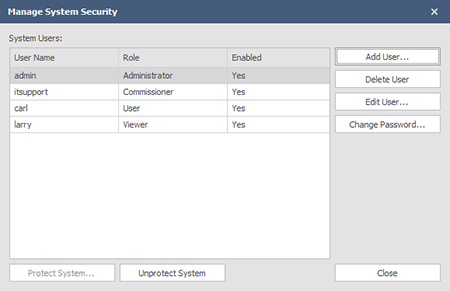
IMPORTANT: Only an Administrator may un-protect a system. Administrator and other user credentials should be kept secure and documented elsewhere as required in the event of personnel changes, etc. that could compromise system security. If those credentials are lost, the there is no recourse other than performing a factory reset on all of the system devices, and then re-configuring the system.
System user permissions are defined in the tables that follow. These apply to protected systems only. To jump to a specific function/action, click the links that follow:
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Configuration |
Configure a system / Reconfigure a system |
Clear the system |
|
|
Administrator |
YES |
YES |
YES |
|
Commissioner |
YES |
YES |
YES |
|
User |
YES |
NO |
NO |
|
Viewer |
YES |
NO |
NO |
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Schedules |
Add or Modify Schedules |
Remove Schedules |
|
|
Administrator |
YES |
YES |
YES |
|
Commissioner |
YES |
YES |
YES |
|
User |
YES |
YES |
YES |
|
Viewer |
YES |
NO |
NO |
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Settings |
Modify Soft Start Settings |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Device Date/Time |
Modify Device Date/Time |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
YES |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
|
|---|---|---|
|
Initiate Firmware Update |
||
|
Administrator |
YES |
|
|
Commissioner |
YES |
|
|
User |
NO |
|
|
Viewer |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Settings |
Update Zone Setting |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
YES |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Settings |
Modify Settings |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Settings |
Modify Settings |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Master User List |
Create and Modify Users |
Remove Users |
|
|
Administrator |
YES |
YES |
YES |
|
Commissioner |
NO |
NO |
NO |
|
User |
NO |
NO |
NO |
|
Viewer |
NO |
NO |
NO |
|
User Role
|
Action |
|---|---|
|
Retrieve Fault List |
|
|
Administrator |
YES |
|
Commissioner |
YES |
|
User |
YES |
|
Viewer |
YES |
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Data |
Modify Data |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Network Settings |
Update Network Settings |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
NO |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve Current Description |
Modify Device Description |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
|
|---|---|---|
|
Initiate Firmware Update |
||
|
Administrator |
YES |
|
|
Commissioner |
YES |
|
|
User |
NO |
|
|
Viewer |
NO |
|
|
User Role
|
Action |
||
|---|---|---|---|
|
Retrieve User Logs |
Clear User Logs |
||
|
Administrator |
YES |
YES |
|
|
Commissioner |
YES |
YES |
|
|
User |
YES |
NO |
|
|
Viewer |
YES |
NO |
|
|
User Role
|
Action |
|
|---|---|---|
|
Retrieve Device Logs |
||
|
Administrator |
YES |
|
|
Commissioner |
YES |
|
|
User |
YES |
|
|
Viewer |
NO |
|
|
User Role
|
Action |
||||
|---|---|---|---|---|---|
|
Retrieve Certificate List |
Export Certificate |
Import Certificate |
Delete Certificate |
Edit 802.1X |
|
|
Administrator |
YES |
YES |
YES |
YES |
YES |
|
Commissioner |
YES |
YES |
NO |
NO |
NO |
|
User |
YES |
YES |
NO |
NO |
NO |
|
Viewer |
YES |
YES |
NO |
NO |
NO |